Overview
Certificates secure device communication through data encryption and other methods as well. For example, X.509 certificate PKI is used to authenticate devices to IoT Hub and secure the IoT Hub endpoints.
 (Screen: Certificates)
(Screen: Certificates)
To begin with X.509 certificate, register and upload X.509 certificates to an IoT Hub. That way, they can be used for authentication of IoT devices to the IoT Hub whenever they connect. The process saves your time and efforts from generating private secure keys for every IoT device. With X.509 CA feature, you need to register the certificate just once. And then use it to connect and authenticate as many devices as possible.
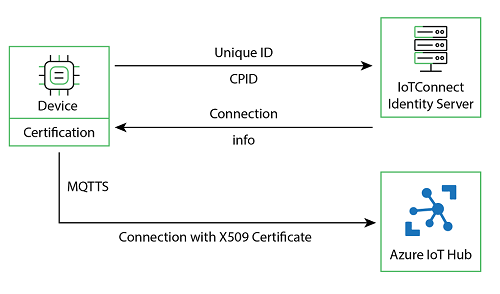 (Screen: Workflow of Certificates in IoTConnect)
(Screen: Workflow of Certificates in IoTConnect)
This article describes device onboarding with an X.509 certificate.
- Register your X.509 CA certificate to IoTConnect.
- Set up a manufacturing supply chain for X.509 CA-based authentication.
- Devices signed with X.509 CA connect to IoTConnect.
The supply chain for X.509 CA-based authentication
Generate an X.509 intermediate CA certificate signed by an existing root CA certificate and upload it to the hub. Once the intermediate certificate is uploaded and verified, as instructed below, it can be used in the place of a root CA certificate mentioned below. Tools like OpenSSL (OpenSSL req and OpenSSL ca) can be used to generate and sign an intermediate CA certificate.
IoTConnect provides the following types of authentication methods:
- Key: This certificate uses the X.509 public key infrastructure standard to associate that key with an identity contained in a certificate.
- Self-signed Certificate: It provides an identity certificate that is signed by the same entity whose identity it certifies.
- CA-signed Certificate: It ensures that the certificate was signed by a trusted signer somewhere in the document.
- TPM: This mainly consists of discrete hardware, integrated hardware, firmware-based modules, or software-based modules.