X.509 certificate PKI is used to authenticate devices to IoT Hub and secure the IoT Hub endpoints. The process begins with registering and uploading X.509 certificates to an IoT Hub which will be used for authentication of IoT devices to the IoT Hub whenever they connect. This authentication process saves you from generating private secure keys for every IoT device. With X.509 CA feature, you need to register the certificate just once, and then use it to connect and authenticate as many devices as you want.
This article describes the onboarding of Device with an X.509 certificate.
- Register your X.509 CA certificate to IoTConnect
- Set up a manufacturing supply chain for X.509 CA-based authentication
- Devices signed with X.509 CA connect to IoTConnect
Register your X.509 CA certificate to IoTConnect
There are three steps need to follow to add the X.509 CA certificate on the IoTconnect.
- Upload your CA root certificate
- Generate Verification code(proof-of-possession)
- Upload Verification certificate
Upload your CA root certificate
You will be able to add a certificate by providing appropriate details from this page. From the Device Certificate List page, click Add Certificate to navigate to the Create Certificate page. You can create a certificate with the below-mentioned details, upload .cer or .pem file.
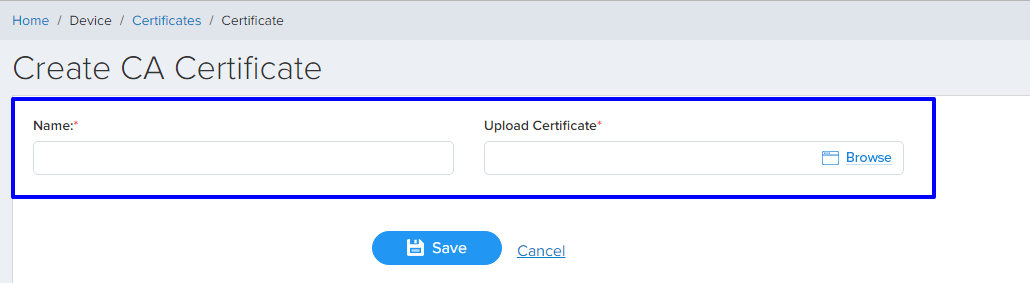
Generate Verification code
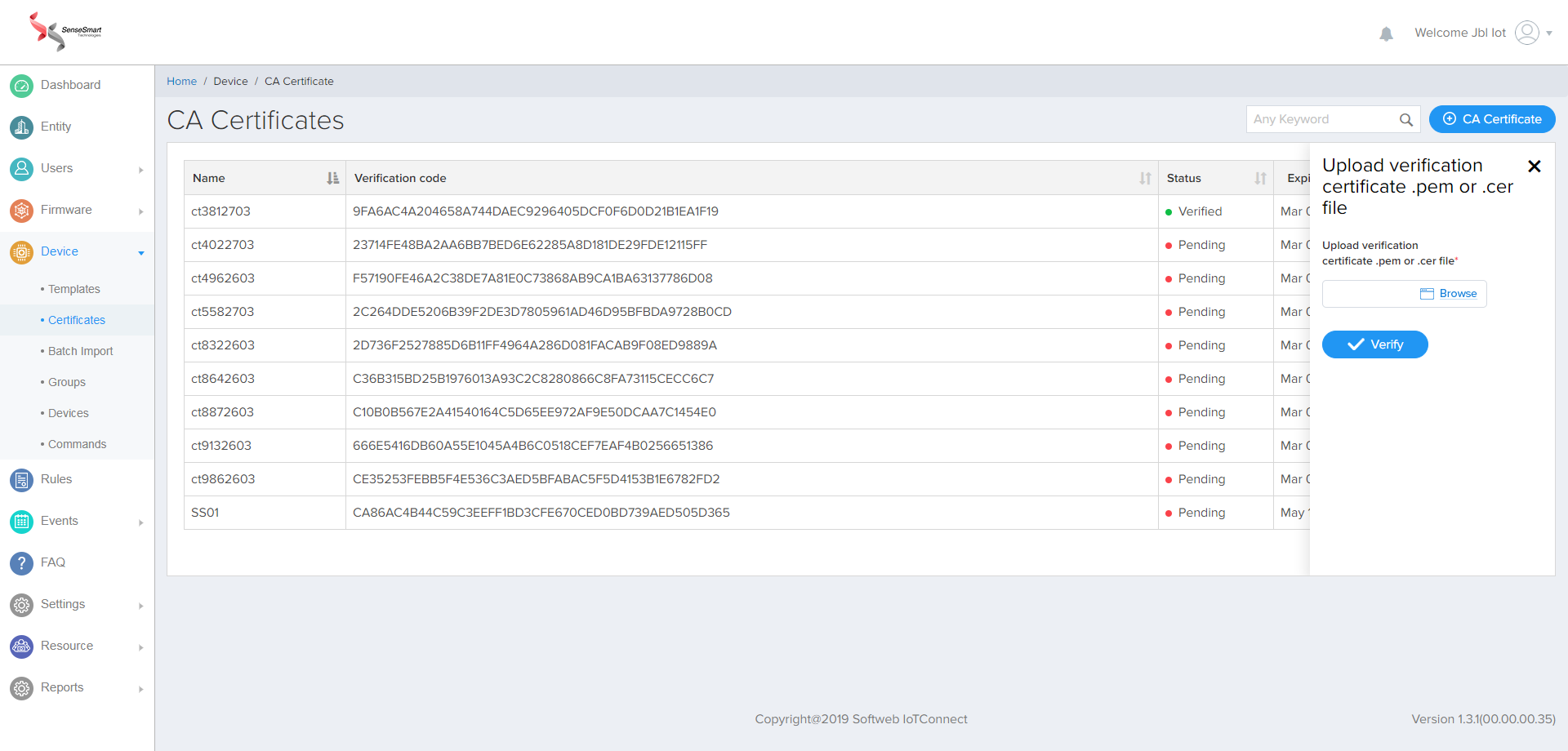
Once you are done with Upload your Certificate, you will get the Verification code
Managing test CA certificates for samples and tutorials. This process signs your verification code with the private key associate with your X.509 CA certificate, which generates a signature. There are tools available to perform this signing process, for example, OpenSSL. This process is known as the Proof of possession. (Microsoft Doc Content.)
Upload Verification certificate
The supply chain for X.509 CA-based authentication
Generate an X.509 intermediate CA certificate signed by an existing root CA certificate and upload it to the hub. Once the intermediate certificate is uploaded and verified, as instructed below, it can be used in the place of a root CA certificate mentioned below. Tools like OpenSSL (openssl req and openssl ca) can be used to generate and sign an intermediate CA certificate. (Microsoft Doc Content)
Devices signed with X.509 CA connect to IoTConnect
To authenticate your X.509 device, you need to first sign the device with the CA certificate. The signing of leaf devices is normally done at the manufacturing plant, where manufacturing tools have been enabled accordingly. As the device goes from one manufacturer to another, each manufacturer’s signing action is captured as an intermediate certificate within the chain. The result is a certificate chain from the CA certificate to the device’s leaf certificate.(Microsoft Doc Content)
NOTE: Leaf device certificate should have CN name same as Device clientID, you can find your device clientID on Device Connection info of device in IoTConnect portal.
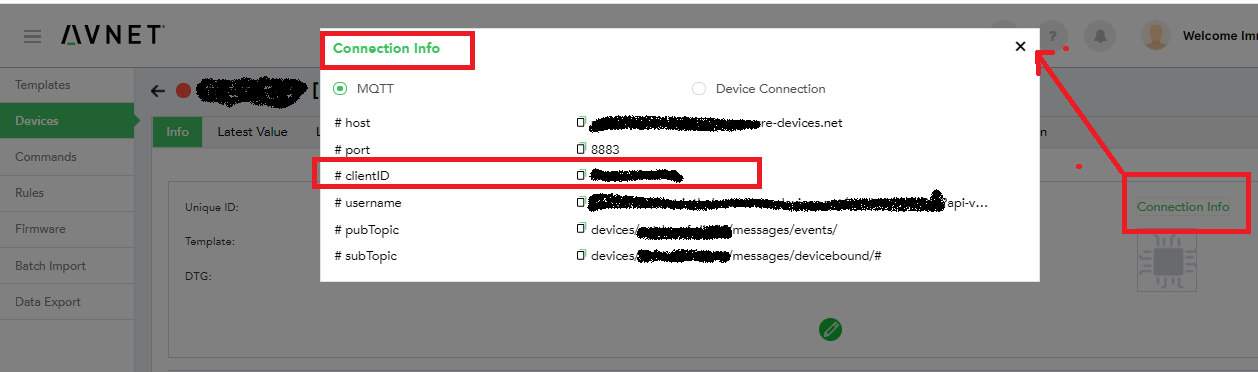
To connect Device with X.509 CA certificate
- You need to create a Template with CA Sign Authentication (see details to create a template).
- Create Device
- Integrate SDK on the device






