There are three major factors that need to be ensured during device authentication:
- The device is genuine
- It is running a genuine software
- It is working on behalf of a trusted user
Here are the three device authentication methods used by IoTConnect to verify any device:
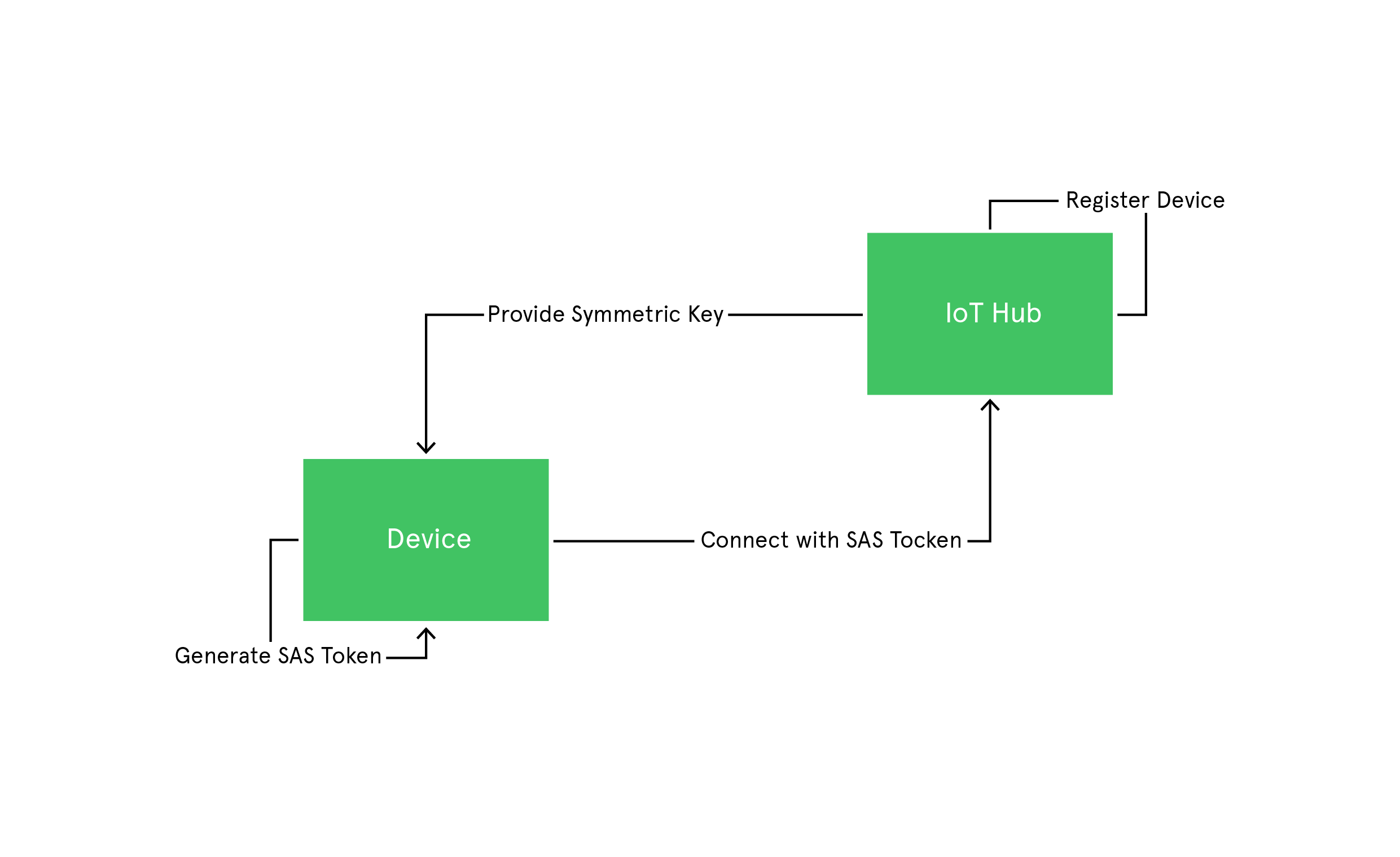
Key-based device authentication
It is one of the simple ways to authenticate any IoT device. Here, SAS tokens are generated using symmetric keys provided during device enrollment. The device then uses this key to generate SAS tokens. These SAS tokens have a hashed signature, which is used to verify the authenticity of these tokens. Once the device is authenticated, these SAS tokens are used to connect to Azure IoT Hub and send messages.
X.509 Certificates
X.509 certificate PKI is used to authenticate devices to IoT Hub and secure the IoT Hub endpoints. The process begins with registering and uploading X.509 certificates to an IoT Hub which will be used for authentication of IoT devices to the IoT Hub whenever they connect. This authentication process saves you from generating private secure keys for every IoT device. With X.509 CA feature, you need to register the certificate just once, and then use it to connect and authenticate as many devices as you want.
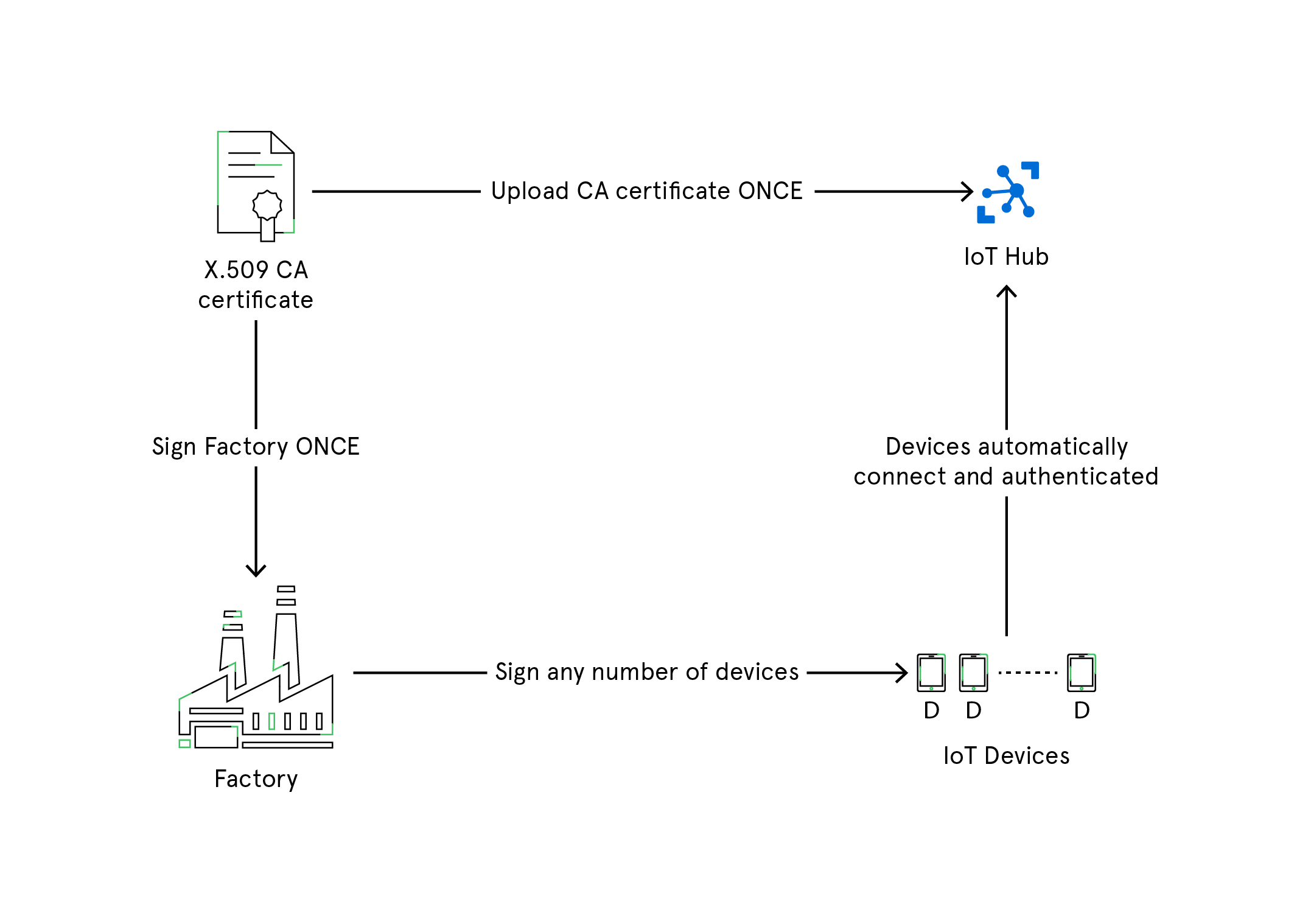
Trusted Platform Module (TPM)
Trusted Platform Module or TPM is another popular way to authenticate devices. It is a type of hardware security module (HSM) where a chip is injected into the motherboard of a device that stores cryptographic keys for authentication purpose. The public portion of the endorsement key contained in the TPM is used to recognize the genuine nature of a TPM and authenticate the device using device provisioning (DPS) service.
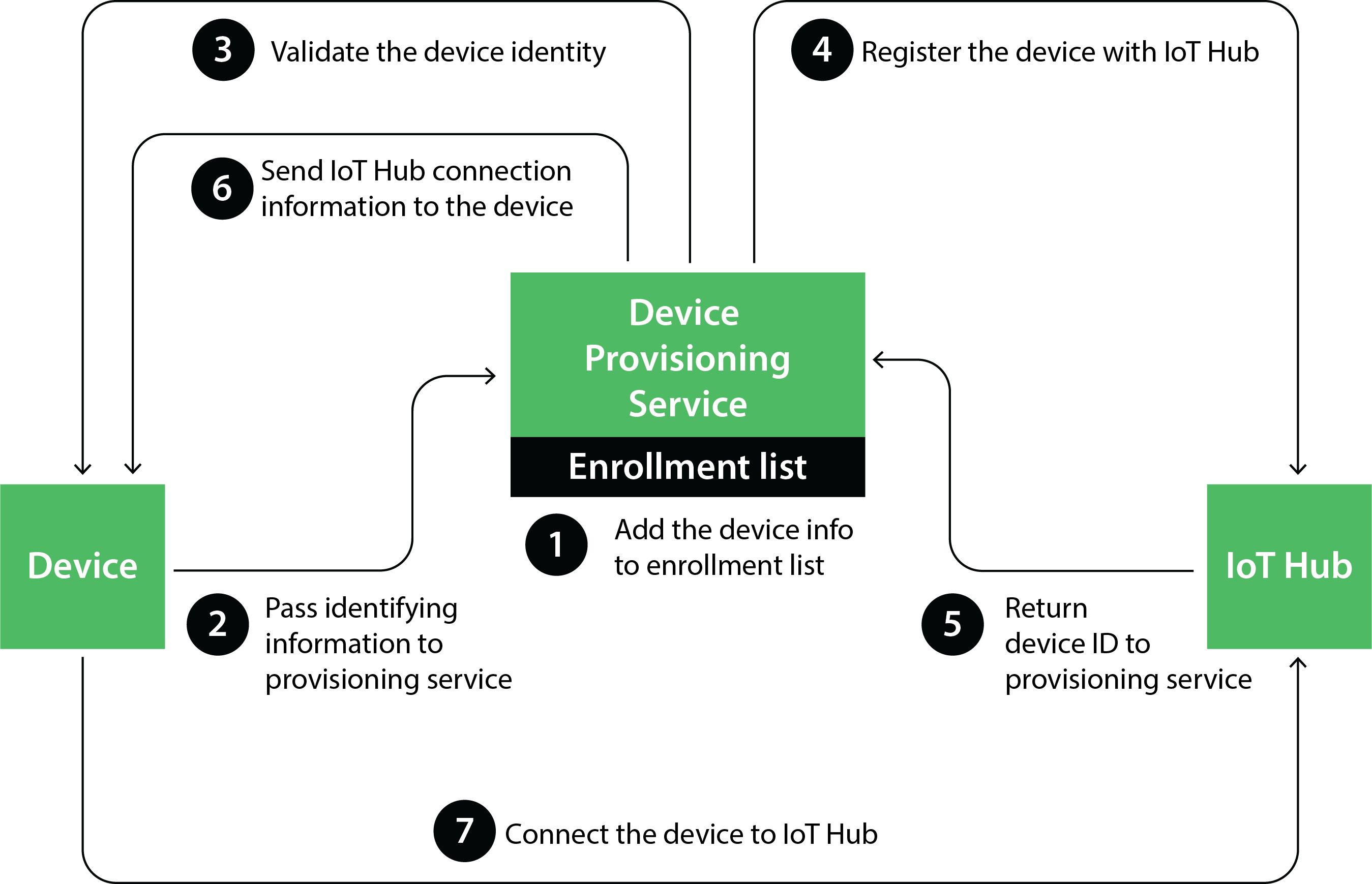
How TPM and DPS improve the authentication process:
- In case of the expiry of the security token used for secure connection with an IoT Hub, the device itself requests for a new token. This saves time from generating and assigning tokens every time they expire.
- As DPS has information about one or more IoT Hubs, it becomes easy to route the devices to the right IoT Hub.
The three authentication methods mentioned above are great to identify and authenticate a device. But it is recommended to use X.509 Certificates and TPM, as replacing symmetric keys is both hard as well as less secure.